How to create & remember a strong password.
It's easy to create a strong password - and remember it. You only need to know how!
Navigating the Sea of Terrible Passwords.
Step 1: Know Your Enemy
Attacks against user passwords can come in all shapes and sizes. If you want to craft a strong password the first step is learning about what kinds of tricks may be used to unearth yours. Here are a few of the main ways that cyber ne’er-do-wells are actively accessing bank accounts, personal emails, and social media profiles.
In most cases attackers have access to a collection of breached password data. These passwords are most often listed in a hashed form, but it is not difficult to uncover the plaintext credentials found within. Once a data breach occurs, the leaked information has become publicly available and is likely not going away. The best course of action for anyone who has their data become public through such a breach is to immediately change their passwords and enable some form of multi-factor authentication. Generally, we recommend our users to activate two-step authentication in our password security guide.
It is important to keep in mind that this video was published in 2016. Computing capability and graphic cards in particular have greatly increased in performance, but unfortunately the average user’s choice of password likely hasn’t kept up with these rapid advancements.
Brute-Force Attacks

Enough chimps with enough time will brute-force your password. Source: Wikipedia
A brute-force attack is an attempt by a malicious actor to test all the possible combinations of letters, numbers and symbols until they determine the password which matches your username. An example of a brute-force attack on a 5 digit password would be an attacker trying:
aaaaa … mmmmm … zzzzz
These attacks have a high rate of success against short passwords which do not use numbers or special characters. Fortunately, these types of attacks can be mitigated by creating longer passwords which utilize a mix of letters, numbers, upper- and lower cases, and special characters.
Dictionary Attacks
The RockYou data leak exposed over 32 million passwords in plaintext. This list comes standard in Kali Linux.
A dictionary attack is a more refined brute-force attack which uses selected dictionary wordlists to test at potential passwords for your account. If your password includes words found in these dictionaries, such as the wordlists found in default installations of mainstream hacking Linux distros, you are susceptible to these attacks. If your password is listed here, change it now!
Phishing Attacks
Phishing attacks are well-known and efficient harvesting techniques which directly target the account user. A cleverly disguised link sent from a trusted source, website, or your IT admin can provide quick access to valid login credentials.
Phishing attacks are not limited to emails, but have made their way into telephone calls, SMS, VoIP, and other messaging services like WhatsApp and Signal. If an attacker is focused on one specific individual these attacks, known as spear-phishing, can be that much more difficult to detect before it is too late.
The best way to combat phishing attacks is staying vigilant. Don’t click on links sent in emails or open unexpected email attachments. If you receive automated emails from your bank requiring urgent action in your account, always doubt that it is actually from your bank. If you believe action might be needed, open a new browser tab and login directly from your bank's website.
Man-in-the-Middle Attacks
How often do you login to the free WiFi at your favorite coffee shop? If you are not careful, you may be connecting your device to a rogue access point instead of that trusty Starbucks connection. Man-in-the-Middle attacks stand between your device and the actual access point, pretending to be someone they are not. These fake networks can eavesdrop and log the traffic that you send and receive through it, including any unencrypted passwords sent along the way.
How to create a strong password
Step 2: What is a strong password?
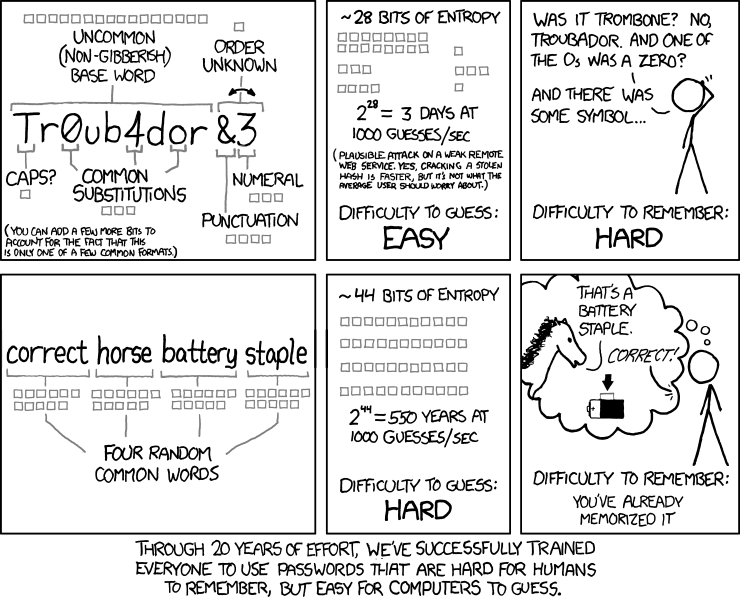
A good password is both: complicated and easy to remember! Source: xkdc.com
The Good:
A strong password must be long enough to avoid being brute-forced. It should be, at least, 12 characters long and include a mixture of letters, numbers, and special characters. It is also important not to use these numbers or special characters in common ways. The seemingly clever choice to swap your o’s with 0’s or your e’s with 3’s is not going to fool anyone out to steal the login information for your bank account.
If you do choose to use a string of random words, they should not be related to each other in order to prevent falling victim to a dictionary attack. Mixing in numbers at random intervals and not always before, between, or after words make them even more difficult to crack. For example “B?r!d7sDri%&veP._otat!oC?8ches” is less likely to be cracked in a dictionary attack than “BirdsFly”.
“B?r!d7sDri%&veP._otat!oC?8ches” may be unlikely to be cracked, but if I fall for a phishing link or get caught in a man-in-the-middle attack human error overrides any mathematical advantage the previous steps have provided.
Again, to create a strong password:
- Use at least 12 characters
- Include upper- and lowercase, numbers, and special symbols
- Do not use dictionary words
- Do not use special characters in predictable ways (H3llo or Pa$$word)
We’ll get to how you can remember this new password later.
The Bad:
If your password shows up in a search at HaveIBeenPwned, you should change it immediately. The Pwned Password is available for a free download and is undoubtedly being used to gain unauthorized access to accounts around the world.
It is crucial to avoid using single words which are quickly brute-forced by any average computer. The password “agoodpassword” can be brute-forced in two days and already appears in 107 data breaches according to Kaspersky’s Password Checker. If we swap the o’s with 0’s, the password will still be brute-forced in two days. Go ahead and try some of these out if you are interested.
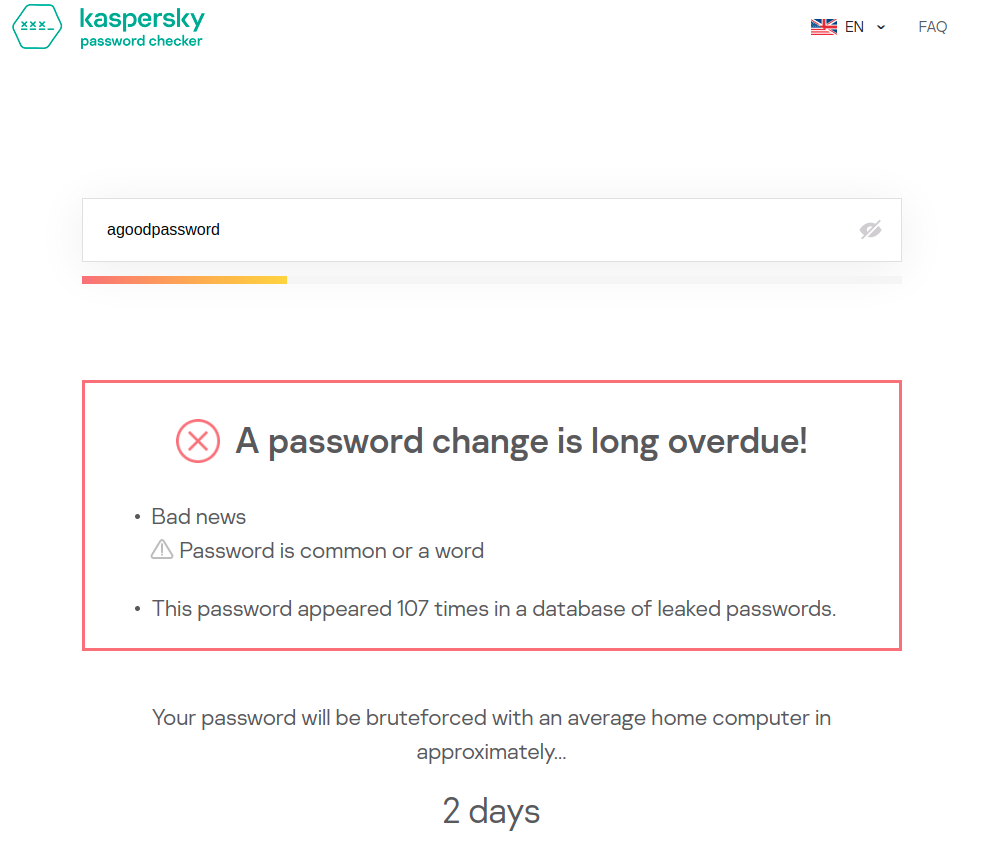
I do not recommend testing your real passwords on a website like this, but it is interesting to see how different combinations impact the strength of a password.
Your password should also not include personally identifiable information, like your first pet, your wedding anniversary or the street which you grew up on. All of this information is readily available with some simple social engineering or a visit to your Facebook page. This means that “amy&bob4ever1997” is a poor choice. Even if it may take “12 centuries” to be brute-forced according to the above strong password checker, a visit to your public social media pages full of pictures posted from that special occasion will reduce that time drastically.
The Ugly:
There are some passwords that will unfortunately never go away. The following list is the top 10 most common passwords according to NordPass.com. If you are using ANY of these passwords, you need to change them, preferably yesterday.
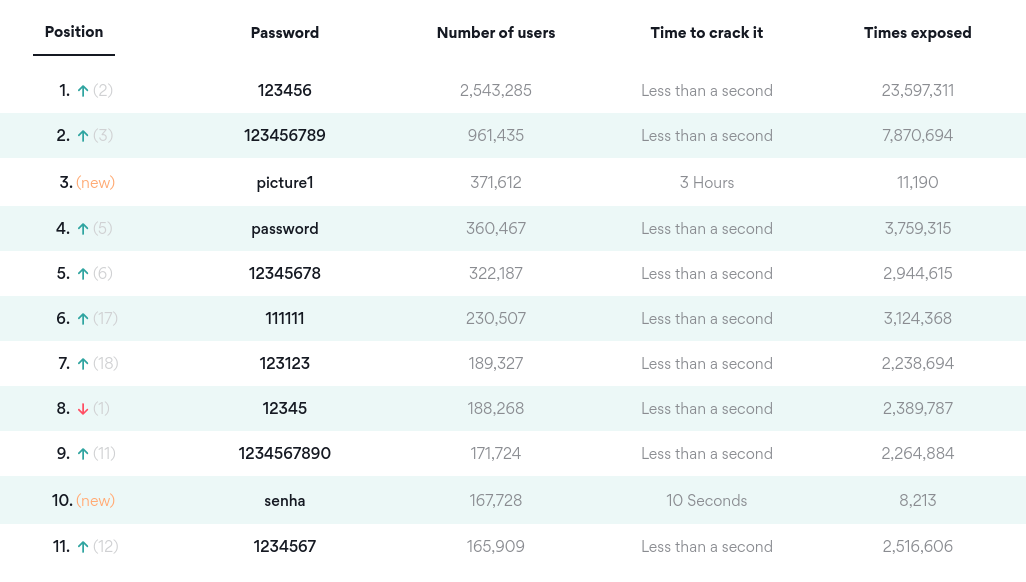
You can find the top 200 most common passwords from 2020 [here)(https://nordpass.com/most-common-passwords-list/).
Step 3: How can you create a strong password?
Now that we have an idea of how to create strong passwords by using at least 12 characters, including numbers, capitalization, and special characters, and avoiding dictionary words or placing numbers in obvious places, this begs the question of how are we going to remember this behemoth of a password?
Mnemonic passwords
One easy tip is to use a mnemonic password. Create a long sentence which will likely be easy to remember: “The duck ran from the one dog while eating 5 purple carrots” can be shortened into a password that looks like “Tdr/n4rom1d00gWe5Pur%Ca&”. This is 24-characters, includes numbers and special characters, and while it may look like nonsense at first glance, it can be remembered by the strange original sentence. This is the same technique that many of us used in math class when trying to remember that pesky order of operations. I’m sure "Please excuse my dear aunt Sally" still holds a place in many memories.
The Diceware Passphrase Generator
Another great way to make easy to remember password with a high degree of randomness is to use Arnold Reinhold’s Diceware method of passphrase creation. This method is designed to maximize the amount of randomness in the passphrase generation process. Why is this necessary? We often think that we might be a bit more clever than we actually are and our attempts at coming up with a truly random list of words falls short of that goal. Our word bank is limited by our education, location, and many other factors which can make our passphrase choices less secure than we might like.
To use the Diceware passphrase system you will first need some dice. (It is important not to use a software based dice program!) Once you have at least 5 dice you will need to download the Diceware wordlist. You can find many Diceware lists to choose from in multiple languages when you search online.
You then roll 5 dice and record the resulting numbers. Reinhold’s own example is as follows:
“Suppose you want a six word passphrase, as we recommend for most users. You will need 6 times 5 or 30 dice rolls. Let's say they come out as:
“1, 6, 6, 6, 5, 1, 5, 6, 5, 3, 5, 6, 3, 2, 2, 3, 5, 6, 1, 6, 6, 5, 2, 2, 4, 6, 4, 3, 2, and 6.
“Write down the results on a scrap of paper in groups of five rolls:
1 6 6 6 5
1 5 6 5 3
5 6 3 2 2
3 5 6 1 6
6 5 2 2 4
6 4 3 2 6
“You then look up each group of five rolls in the Diceware word list by finding the number in the list and writing down the word next to the number:
1 6 6 6 5 cleft
1 5 6 5 3 cam
5 6 3 2 2 synod
3 5 6 1 6 lacy
6 5 2 2 4 yr
6 4 3 2 6 wok
“Your passphrase would then be: cleft cam synod lacy yr wok”
The result is a long, highly randomized passphrase, which is somewhat easy to remember. This method makes quite long passwords which prevents brute-force attempts and if combined with randomly placed symbols and numbers (not between the words) can also be made strong against dictionary attacks. This method has the added bonus that, if you want to make the password more difficult to crack all you need to do is add additional words!
The Sticky Note
I guarantee you that if you enter any mid to large sized office building, someone has written down their password and left it in an unlocked desk drawer. This is never a safe security practice. Don’t be the person whose laziness leads to a company-wide security breach.
It is important that IT professionals realize that their users are the first line of defense against unwanted access into your network. Proper training for your employees is crucial to prevent slip- ups like this from happening. IT teams need to work with their users to combat threats to company data. Numerous harmless reports of an obvious phishing email are far less annoying than trying to undo the damage of a ransomware infection.
Password Rotation Policies
A leading cause for users writing down their credentials where they can be easily discovered is the out-dated recommendation of password rotation policies. Fortunately, these days are gone and NIST no longer recommends these mandatory password rotations. These policies often led to users choosing simpler passwords with only minor variations. These password choices were that much easier to brute-force or led to users writing down their passwords and storing them insecurely because they have difficulties remembering the new credentials.
Passwords should be changed in the event of a breach, accidental exposure, or if the user has forgotten it.
Don’t Recycle Passwords
Reusing passwords is the easiest way for a malicious actor to move from your compromised Facebook account to your bank account. It is crucial that passwords (and usernames) are not used between services. This may seem daunting but there are various options which can make keeping multiple strong passwords easier.
There are many websites which offer “new creative and clever passwords for 2021”, but choosing any pre-existing password or username you may see online (or even those in this post) poses a security risk.
Remember, a good password should be like toilet paper: strong and only used once.
Saving Passwords in the Browser
One option for saving passwords it to simply save them in your internet browser, be it Firefox, Chrome or Safari. Many of these passwords can then be linked to an account which can be synced between devices in the event of a replacement.
As convenient as this may sound, this is not recommended if you cannot guarantee that no one can gain unwanted access to your device. A quick trip to the preferences window results in a full list of saved passwords which are stored in plain-text for the world to see. This is less than ideal.
Password Managers
A more reliable means of storing your passwords is through the use of a password manager. There are more password managers than can be adequately discussed in this blog post. Password managers store all of your various login credentials in one central location and (ideally) encrypt all of that data. In the event that your device is stolen, these passwords and usernames cannot be uncovered without first unlocking your password manager.
These programs have the added benefit of including password generators which can create and save random passwords which are beyond any reasonable expectation of human memory. This saves you the trouble of coming up with strong new passwords on-the-spot.
If you do choose to use a password manager it is absolutely necessary that you create a strong password. This password acts as the key which unlocks your entire digital life and should be treated as such. Fortunately, many of these programs also support multi-factor authentication which gives your data a much needed extra layer of protection.
I have collected some best password managers in another post where I also explain why to start using password managers now!
Some of these options are free and open source, while others require a subscription in order to use their services. If you are a Mac or Linux user, your device comes pre-installed with a keychain program which also allows you to store your login credentials. These are convenient features, but do not provide the same degree of cryptographic security as these third-party password management solutions.
Stay Safe and Happy Browsing!
If you follow these steps in creating a stronger password and storing it securely using the password manager of your choice, you have made yourself a much more difficult digital target. When it comes to cybersecurity there is no case of bulletproof protection, but if malicious actors are choosing who to target, your account with a strong password and multi-factor authentication will be much less appealing.
With these tips you can step up your digital security and surf with the web with greater confidence that your online accounts and your personal information are protected.
Check out our email security guide as well. It explains how an email account is the gate to your online identity and how you can further improve your online security by making some smart choices.











