Innovative encryption: Tutanota makes encryption easily accessible to all.
How Tutanota, the innovation leader in secure communication, protects your private key and your data with top-notch encryption.
Note: This blog post is no longer updated. For up-to-date information about Tutanota's encryption, check our encryption page.
The future of encryption
In the future, encryption faces a huge challenge: quantum computers.
Currently used encryption algorithms rely on the fact that state-of-the-art computers need an incredibly long time to calculate for being able to break the encryption. This is why current encryption can be considered safe and unbreakable.
The innovation of quantum computers will change this. These computers are so powerful and can run so many calculations in parallel that currently used encryption algorithms (e.g. in PGP) will no longer withstand attacks from quantum computers.
In the future, to protect data against growing threats we need innovative approaches to encryption, for instance post-quantum cryptography, quantum key distribution, forward secrecy or homomorphic encryption. All of these will be important to keep data safe from preying eyes while technology advances.
Tutanota as the innovation leader in secure communication is already tackling this challenge with post-quantum secure encryption. We have carried out a research project to find post-quantum secure algorithms to update the encryption and keep data secure - also in the future.
By now, we have a running prototype that can encrypt emails with standard encryption algorithms as well as post-quantum secure algorithms in a hybrid protocol, the most innovate encryption to date.
The post-quantum secure algorithms of our prototype have also made it to the next round of NIST research, which means they are very likely to be chosen as the new standard for post-quantum secure algorithms.
This is great news for our research project!
Innovative encryption
Explanation of Tutanota's encryption process
Tutanota's innovative encryption method secures your private key so that you - and only you - can access your data from any device.
Tutanota uses an innovative encryption method to secure your data easily. Tutanota is the only email service that automatically encrypts all emails, all calendars and all contacts by default. Key generation, key handling, key exchange – all of this happens automatically in the background, yet, the private key is still only accessible by the user.
When a user registers a secure Tutanota email account, the browser, Tutanota app, or desktop client automatically generates a private and a public key locally on your device. The private key is encrypted with the help of the user’s password before it is transmitted to Tutanota’s servers in highly secured data centers in Germany.
While many seemingly secure cloud services store private keys openly on a central server, this has never been an option for us.
Read here why a private key must not be stored on a central server unencrypted.
Private Key is encrypted with user’s password
In Tutanota, the private key is encrypted with the user’s password so that only the user can access it. No one else, not even we as the developers of Tutanota, can access the private keys stored encrypted on our servers.
How is the password secured in Tutanota?
As the user's password is central to the security of the encrypted data stored in the Tutanota mailbox, we have to make sure that the password is secured at all times. Tutanota never sends the password to the server in plain text in order to authenticate the user.
To secure the login password, Tutanota uses bcrypt and SHA256. Thus, the login password is only used indirectly to authenticate the user with the server and to encrypt / decrypt the private key.
This is shown by the following picture and explained in the text below:
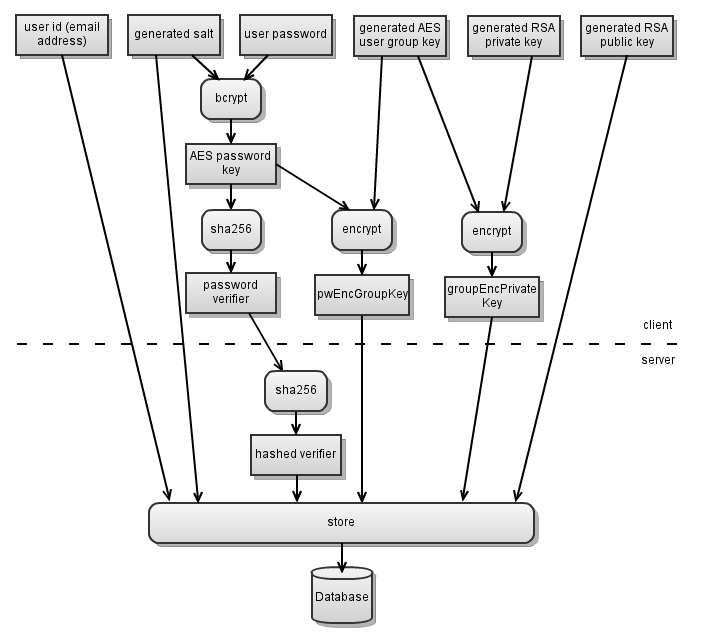
Bcrypt modifies the password so that it becomes the “AES password key”. This AES password key is used to encrypt the private RSA-key (though via an indirection with the private symmetric “AES user group key”).
The AES password key itself, however, is not used to authenticate the user with the server, but it is hashed to become the “password verifier”.
This password verifier is then transmitted to the server to authenticate the user. The server itself only stores the password verifier as another hash ("hashed verifier") so that it is impossible to use the persistent data on the server to login.
The password verifier is cryptographically independent from the password key so that the password verifier can not be used to decrypt any data. The password verifier is transmitted to the Tutanota server secured with TLS encryption.
Should a third person gain access to the password verifier via a TLS vulnerability, he would not be able to gain access to the private key or to the end-to-end encrypted data stored in the encrypted Tutanota mailbox.
The decryption process takes place locally on the device of the user once the user has been authenticated with the server.
Standard password reset functions allow the provider to access your mailbox
Standard reset functions used by all email services give the provider access to the mailbox as they could use the reset themselves. That’s why a standard reset function is not possible in Tutanota. Instead Tutanota uses a secure reset function, one which would not involve us in the reset process to make absolutely sure that we can never access your secure Tutanota mailbox.
We have built Tutanota with innovative encryption in order to make encrypted emails as easy as possible without any compromise when it comes to security. This is also why we have published the Tutanota client as well as our Android and iOS apps and our dedicated desktop clients as open source.
As all the encryption takes place locally on your device, others can check the code and make sure that it is not being compromised. You can check our code on GitHub or build your own Tutanota client locally.
Desktop email clients for best security
At Tutanota, we take every detail into consideration and make sure that your data is always kept secure. For this reason, we also do not offer the option to use standard mail clients via IMAP/Pop as Tutanota’s built-in encryption would not work. On top of that, the emails stored in these mail clients would be stored in plain text (unless you encrypt your local hard drive yourself).
Instead we have developed open source desktop clients for Linux, Windows and macOS that are the most secure option to use Tutanota.
Read more on the benefits of the Tutanota desktop clients.
Encrypted search for maximum security
Building a search feature for Tutanota was one of the greatest challenges to develop so far because we can not - as other mail services do - search data on the server. On the Tutanota server all data is encrypted, thus, we can not search it there.
Instead, we have developed an encrypted search feature that lets you search your mails locally on your device via an encrypted search index. We also believe that security and privacy go hand-in-hand. This is why Tutanota is a perfect choice when your are looking for an anonymous email account.
Why Tutanota does not rely on PGP
Tutanota uses standard algorithms also being used by PGP (AES 128 / RSA 2048) for encrypting the entire mailbox. Tutanota does not use an implementation of PGP because PGP lacks important requirements that we plan to fix with Tutanota:
PGP does not encrypt the subject line (already achieved in Tutanota),
PGP algorithms can't be easily updated (which we need to do when updating to post-quantum secure algorithms),
PGP has no option for Perfect Forward Secrecy (already achieved in our post-quantum prototype).
In Tutanota we can easily update the algorithms, and we plan to replace the current algorithms with quantum secure ones in the near future. The flexibility of Tutanota enables us to integrate an encrypted calendar, encrypted cloud storage and many more features much easier and faster than it would have been possible with an implementation of PGP. With the update to post-quantum secure algorithms we will also add support for Perfect Forward Secrecy to Tutanota.
Secure email as easy as possible
At Tutanota we have developed an encrypted mail service that combines a high level of security with a high level of comfort.
With its innovative encryption, we enable everyone to send confidential data securely via mail.
With Tutanota you will never have to worry about the confidentiality of your private mails.
Get your own secure mail account now!