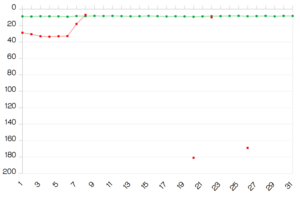
The Microsoft database hack shows that data stored in the cloud must always be encrypted end-to-end.
While politicians still ask for 'legit access' to fight CSAM, the latest Microsoft hack shows that any data stored without encryption is always at risk.

Microsoft Azure hack - what happened
IT security specialist Ami Luttwak from Wiz discovered the vulnerability in the Azure Cosmos DB Jupyter Notebook Feature on Aug. 9 and reported it to Microsoft three days later. Microsoft published this statement saying it immediately fixed the issue. Microsoft thanked the security researchers for their work as part of the coordinated disclosure of the vulnerability. Microsoft also told Wiz via email that it planned to pay out $40,000 for reporting the vulnerability.
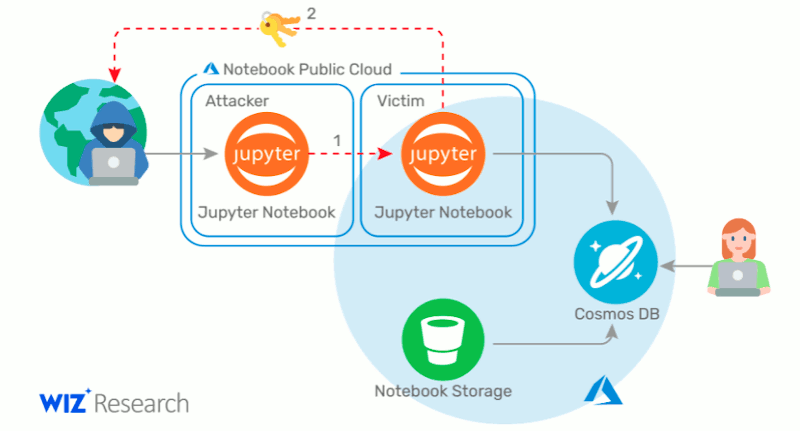
Explanation of the Cosmos DB hack via the Jupyter feature, source.
On Aug. 26, Microsoft notified several thousand of its cloud customers affected by the issue via email. In the message, the company warns its customers that attackers had the ability to read, modify and even delete all of the main databases. Luttwak managed to gain access to primary read-write keys, which he used to gain full access to customer databases. Because Microsoft could not change these keys itself, the company asked its customers to take action and exchange this primary key of CosmosDB as a precaution. Although the security hole has already been closed, customers should take this step to finally prevent a possible compromise of the databases. Microsoft further writes in the message that they have found no evidence that third parties (with the exception of Wiz) have accessed the keys.
Microsoft fails to inform all customers
Luttwak told Reuters he criticized Microsoft's warnings to its customers: The company had only written to customers whose vulnerable keys were visible in the same month that Wiz discovered and investigated the problem. Attackers, however, would have been able to view keys from many more customers because the vulnerability had already been introduced in 2019 when the Jupyter feature was first released. Every Cosmos DB account that uses that feature is potentially at risk. Starting this February, every newly created Cosmos DB account had the notebook feature enabled by default for at least three days and their Primary Key could have been exposed even if the customer was not aware of it and never used the feature.
Since the primary key is a long-lasting secret, which does not update automatically, a potential attacker might still be able to abuse a key once obtained even if the affected company turns off the Jupyter feature in Cosmos DB.
Despite that, and despite criticism from Wiz, Microsoft had not informed all customers who did turn on the feature called Jupyter Notebook to Cosmos DB. When asked about this, Microsoft only told Reuters that it had informed potentially affected customers, but did not explain the statement further.
The U.S. Department of Homeland Security's Cybersecurity and Infrastructure Security Agency used stronger language in a bulletin, making clear it was speaking not just to those customers that had been notified, but to everyone using Azure Cosmos DB:
"CISA strongly encourages Azure Cosmos DB customers to roll and regenerate their certificate key".
You can find information on how to regenerate the key here.
Worst imaginable cloud vulnerability
Luttwak said: "This is the worst cloud vulnerability you can imagine. This is the central database of Azure, and we were able to get access to any customer database that we wanted."
For European Azure cloud customers who have personal data stored in a Cosmos DB instance, there is also the question of whether a precautionary GDPR notification must be sent to the responsible data protection authorities within 72 hours due to a possible security incident.
This Microsoft vulnerability is a nightmare to any company using Cosmos DB. Yet, due to its popularity thousands of companies, among which are many global players including Fortune 500 companies, do use Miscrosoft's Azure Cosmos DB to manage massive amounts of data from around the world in near real-time.
And their data might now be at risk of getting hacked, stolen or even deleted.
Encrypt is all
To reduce the likelihood of such threats, companies that want to move their data to the cloud have only one option: Encryption. And by encryption, we do not mean server-side encryption. We mean true end-to-end encryption where no one - not even the service provider - can get hold of the secret key.
The hack of Miscrosoft's Azure database shows once again that encryption is the best tool we have to fend off malicious attackers and to keep our data safe.
When data is stored in the cloud, the only way to properly protect this data is end-to-end encryption - free from any kind of backdoor.