
FAQ
Security and Privacy
• What encryption algorithms does Tuta use?• Does Tuta log IP addresses or can I use my encrypted mailbox anonymously?• How are my emails encrypted with Tuta?• Is my address book within Tuta encrypted?• Where does the encryption process take place?• How can I view headers in my encrypted mailbox?• Do you delete inactive accounts / recycle email addresses?• Where are my keys generated and how is my private key secured?• Why is automatic image loading blocked in Tuta Mail?• One of my emails has a warning saying mail authentication is missing or failed. What does it mean?• One of my emails is displaying a phishing warning. What does it mean?• Where are the Tuta servers located?• Can I disable sessions remotely (session handling)?• What is encrypted and what can you read?• Where can I report a security issue or a vulnerability that I found in Tuta?Your Tuta Password
• Unlock the Tuta app with a pin, or biometrics (fingerprint, Face ID)• How do I choose a strong password?• When I log out of Tuta, the browser or app always logs in again. What can I do to stop this?• How does the passphrase generator work?• What hashing function is used for the password?• Tuta secures my private key with my password. Can you access my password?• My password was stolen. What should I do now?• Where can I view my recovery code?Security and Privacy
For email encryption between users, Tuta uses a standardized, hybrid method consisting of a symmetrical and an asymmetrical algorithm. Tuta uses AES with a length of 256 bit and RSA with 2048 bit or a combination of ECDH (x25519) and Kyber-1024 (for quantum-safe accounts). Emails to external recipients are encrypted symmetrically with AES 256 bit.
By default, we do not log IP addresses when you log in or when you send an email. The IP addresses of sent and received emails are stripped so that your location remains unknown.
We only log IP addresses of individual accounts in case of serious criminal acts such as murder, child pornography, robbery, bomb threats and blackmail after being served a valid court order by a German judge. You can find details on this as well as on German data protection rights on our blog.
Learn on our blog how Tuta fights illegal mass surveillance by providing an anonymous email service. Upon registration you do not need to provide any personal data (e.g. no phone number required). We will also make it possible to pay for Tuta with Bitcoin.
Tuta automatically encrypts all emails stored in your mailbox. Emails between Tuta users are automatically encrypted end-to-end, and emails to external users can be secured with the help of a password. Here we explain the differences between a confidential (end-to-end encrypted) and a non-confidential email.
Independent of the end-to-end encryption, the transport between the client and Tuta servers is secured with TLS to maximize security.
Watch our YouTube email encryption guide for Tuta - the quickest email encryption guide you can get!
A deleted email address (also if it is an alias) will not be recycled for security reasons. There must be no possibility that someone else is able to register your previously used email address, and then, by accident, receive a confidential email that was meant for you.
Free of charge accounts are deleted after an inactive period of six months. A regular login is necessary to prevent automatic deletion. We delete such accounts for security reasons and also to allow us to offer free of charge Tuta accounts at all. However, the email addresses of such deleted accounts may be taken over into another paid account and re-used as email aliases or additional user addresses if you still have the valid login credentials.
To re-use the email address of the inactive account
- You need to create a paid email account (or use any paid Tuta account you already have as the target account).
- Login to your lost account.
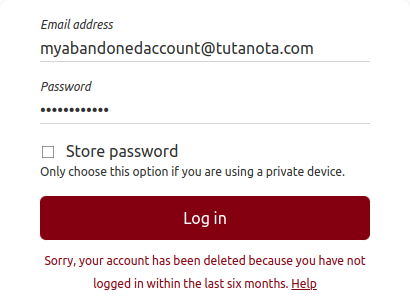
- Click on 'Help' as you can see in the screenshot above.
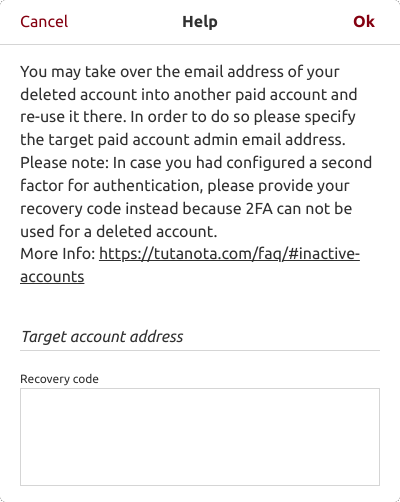
- Enter the 'Target account address' (and - if you enabled two-factor authentication - the recovery code of the lost address).
Then you can add the lost address(es) as an alias (or user) to the target email account. We call it merging of addresses.
Your private and your public keys are generated locally within your browser upon registration. Your private key is encrypted with your password. This way your login password receives the status of the private key. The key is encrypted so strongly that only you can use the key for encrypting and decrypting data. This is why a strong password is essential. An automatic password check on the client makes sure that you use a strong password. Your password is never transmitted to the server in plain text. It is salted and then hashed with Argon2 locally on your device so that neither the server nor we have access to your password. With this innovative design you can access your encrypted inbox from any device (desktop, mobile) easily.
Tuta does not load pictures automatically when you open an email. When you load external images manually, please note that
- someone knows that you read the email.
- someone may add cookies to your browser (if your browser is not configured to reject them).
- someone may track your location with your IP address.
- someone may track the parameters of your device.
Here we explain how to display external images. Please read here how we make sure that you can use Tuta as an anonymous email service.
We require all messages to be authenticated. Without authentication, the email could be coming from anyone or could be modified so you should always treat such emails with scrutiny. If you see a message where the authentication has failed (red warning banner), you should be especially careful as it means that this email was likely faked.
Phishing is a name or type of online scam in which criminals try to look like a legitimate sender in order to get your data such as credentials or credit card data. Phishers use very sophisticated psychological techniques and develop very realistic copies of real websites and emails.
If you see a phishing banner, it means that some parts of this email match our phishing signatures after other users reported similar emails as phishing. Please be extremely careful with such messages. Usually, phishing emails contain a special link to the website which looks real but it actually is not. If you think that the email is legitimate and you opened the link, please make sure to check the full website URL: Check that you see all of it, sometimes only one part or one character may be swapped. Here is more information on how to prevent email phishing attacks.
You can mark an email as not phishing so you will not see the warning message anymore for this email.
We never send you emails with links where you need to type in your password. We encourage you to always protect your login credentials with 2FA as this makes it close to impossible for an attacker to log into your account.
If you've already fallen for a phishing attack, please check this FAQ.
The Tuta servers are located in secure and ISO27001 certified data centers in Germany. All saved data are subject to the strict German privacy protection laws. Independent of that all data is end-to-end encrypted and cannot be read by the Tutao GmbH as the provider or by any third party.
Yes. You can view and remotely close active sessions under Settings -> Login.
Check our How-to to learn how to enable storing of closed sessions to monitor whether someone else has access to your account. To guarantee the users' privacy, we have implemented the feature as follows:
- The IP address is stored encrypted, and only the user can decrypt this information. No one else - not even we at Tuta - can access this information.
- IP addresses are only stored for one week and then automatically deleted.
Tuta encrypts all data stored in your mailbox (contacts, emails, email signature, inbox rules, invoice data, payment method, certificate, and private keys of your own domains). When sending an email, Tuta encrypts the subject, content, and attachments automatically.
You can find a detailed explanation about what is encrypted in Tuta on our security page.
We can read only the following metadata:
- sender email address
- recipient email address
- date of the email
We are looking into possibilities to hide the metadata in the future as well.
Thank you for taking the time to report a vulnerability. If you have found any security issues, please send us an email in either English or German with a detailed report in order for us to fix them.
We at Tuta take utmost care to secure your mailbox to the maximum. The Tuta code is open source and published on Github, and we invite all security experts to review it.
Your Tuta Password
You can secure the stored app login with a pin, pattern or biometrics (fingerprint, Face ID, etc.). Please go to Settings -> Login -> Unlock method to activate this.
This option will only show after you have stored your login credentials in the Tuta app. Upon login tick the checkbox 'Store password' to store your login credentials.
Tuta uses a password strength indicator that takes several aspects of a password into consideration to make sure your chosen password is a perfect match for your secure email account. You can find additional tips on how to choose a strong password here.
Tuta has no limitations in regard to the password length or used characters; all unicode characters are respected.
If you click on 'Logout', you log out. Please note: If you have previously saved the password, you are now logged out, but the password is still saved for automatic login. To 'unsave' the password, please log out. The login screen appears, click on 'More' and 'Delete credentials'.
A secure password is one that is random enough that it cannot be guessed in a feasible amount of time. But random strings of alphanumeric characters are hard to remember. That's why we have implemented a passphrase generator that finds a good balance between security and memorability. The generator chooses six easy words from a huge curated list and outputs a passphrase that is secure as well as easy to type and remember. Here are more tips on how to create and remember a strong password.
Your password is salted and hashed with Argon2 on your device before being transmitted to Tuta. Argon2 is the most reliable method because brute-force attacks need much more time in comparison to conventional methods such as MD5 or SHA. With this method, we guarantee an integrated confidentiality and we allow you to access and decrypt your emails from desktops and mobile devices instantly.
No. When a password is used for authentication (login), it is not necessary that it is known to the server you want to authenticate with. The server only needs a fingerprint (hash) of your password. With Tuta, your hash for authentication is calculated by your browser and only the hash is being sent. Your password never travels the Internet in plain text and it is never seen by our server. As hashes are non-invertible, the server is unable to reconstruct your password from the hash. The server is not able to decrypt your message, but it is still able to log you in.
Recommended for further reading: Learn how Tuta automates the encryption process while leaving you in full control of your encrypted data.,
If you think your password was disclosed to someone else but you can still log into your account, please do the following:
- Change your password in 'Settings' -> 'Login' -> 'Password'.
- Update your recovery code in 'Settings' -> 'Login' -> 'Recovery code'.
If the attacker had been logged in as well, changing the password automatically logs them out.
We encourage you to always use 2FA with your accounts as it makes it close to impossible for an attacker to log into your account.
If you can not log into your account anymore, please check this FAQ.