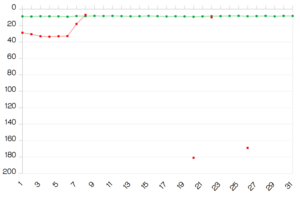
Best of backdoor fails in recent history.
Backdoors: Will they help to catch criminals or will they help criminals?

Best of backdoor fails
Microsoft database hack
The Microsoft database hack in August 2021 was described as one of "the worst cloud vulnerabilities you can imagine". Security experts discovered a vulnerability (not a built-in backdoor) in the Microsoft Azure infrastructure that enabled them backdoor access to modify and delete data of thousands of Azure customers. The security company was able to get access to any customer database that they wanted via this vulnerability.
Microsoft Exchange hack
Earlier this year, it was also Microsoft that had to publish bad news to their customers: In January 2021 several zero-day exploits were reported to Microsoft, which allowed malicious attackers to remotely access Microsoft Exchange servers. However, unpatched Exchange servers are still vulnerable to the attacks. Via this vulnerability companies' email systems were targeted to exfiltrate "information from a number of industry sectors, including infectious disease researchers, law firms, higher education institutions, defense contractors, policy think tanks and NGOs."
Intentionally built-in backdoors
Apart from such vulnerabilities which function as backdoors for malicious attackers online, there are also intentionally built-in backdoors. These are the worst as they could have been easily prevented has the companies in question not built the backdoor.
However, Secret services gladly use such backdoors for espionage purposes, and - as the following cases will show - have actively pressured companies to include backdoors into their products.
Probably everyone still remembers the high-profile case of the Swiss Crypto AG that was owned by the CIA (and earlier also by the BND) to spy on other countries' secret communication. This company successfully sold secure communication tools, particularly to governments around the world, promising that all communication would be securely encrypted. In truth, the CIA was able to listen in on the secret communication by the governments using Crypto AG products.
Huawei is also repeatedly being accused of having a backdoor installed so that the Chinese government can spy on all Huawei customers. This is heavily debated as Huawei is an important player in current 5G project around the world.
Most popular, however, when it comes to intentionally built-in backdoors is the NSA. They were responsible for several high profile backdoor fails - and continue to pressure US tech companies to cooperate with them.
NSA backdoors
Juniper backdoor fail
One of the best known backdoor fails is the one by Juniper Networks. In 2017, cryptologists and security researchers documented a high-profile crypto-crime, which was only possible due to a buil-in backdoor by Juniper itself. In 2008, Juniper hab built a backdoor into its own operating system ScreenOS, which could be used to read the entire encrypted VPN traffic of the devices if an internal parameter called Q was known. This was a so-called "Nobody but us" backdoor (NOBUS).
Then in 2012, unknown hackers broke into Juniper's network. They apparently succeeded in changing the source code of ScreenOS and the parameter Q there. They only changed the lock on the existing backdoor. This meant that someone else was able to read the encrypted VPN data in plain text.
It is not known to this day who took over this built-in backdoor. Juniper itself didn't notice the embarrassing expropriation of the NOBUS backdoor until three years later and responded with hasty emergency updates in December 2015.
RSA and the random number generator
The security company RSA received 10 million US dollars from the NSA for including the random number generator Dual Elliptic Curve (Dual_EC_DRBG) in the crypto library BSafe. The 10 million was well invested. For years, RSA (knowingly) sold its crypto library with this backdoor, which their customers then in turn built into their products.
In addition, RSA made sure that the Dual_EC_DRBG, which is actually known to be broken, was included in open standards by NIST, ANSI and ISO. The whole thing was exposed by internal NSA documents published by Edward Snowden in 2013.
Chinese hackers at Google
In 2010, Google had to admit that hackers had broken into its email service Gmail. It is fairly certain that these were Chinese hackers on a political mission. What is less known is that these hackers used a very special method to gain access to Gmail accounts, which is not readily available even on the Google network: To do so, they used a backdoor that Google had built in only for government-legitimized access to emails - so-called lawful interception - by law enforcement agencies.
Encryption backdoors are vulnerabilities
This short compilation of best of backdoor fails - I am sure there are more backdoors being exploited - show that we need strong protection tools to defend ourselves and our sensitive data on the web.
This summary of best of backdoor fails substantiate the fact that backdoors for the 'good guys only' are simply impossible.
Backdoors, even if meant to be only used by law enforcement agencies to catch criminals, open the doors widely to any criminal attacker online and leave ourselves vulnerable to multiple threats. In consequence, backdoors must be viewed just like any other vulnerability. We must understand that any encryption backdoor is a severe security risk and must never be allowed.
Instead of calling for more surveillance as is often done in the ongoing crypto wars, politicians must advocate for everyone's security on the web - and by doing so they need to be honest:
It is not possible to get more security by weakening security.