Threat Modeling In 2024: Your Guide For Better Security
Threat model best practices to evaluate your personal cybersecurity and privacy threat landscape.

Table of Contents:
- What is threat modeling?
- Industry Standards
- Security and Privacy
- Building your privacy threat modeling
- 3 Steps to increase your security and privacy
When it comes to cybersecurity, there are two things that seem to pop up in every discussion, threat modeling and quotes from Sun Tzu's The Art of War. But what is a threat model and what do security experts, DevOps teams, and other figures in the information security space mean when they talk about the importance of threat models, its analysis and its different stages? This guide will help you to quickly understand threat models, how you can apply these to your own life and how they help you to navigate the web more securely.
What is a threat model and what is the threat modeling process?
There are a multitude of different methodological approaches, processes, and methods to threat modeling, but they all agree on a few tenets
Threat modeling is a structured process with the goal to identify security needs, determine security threats and vulnerabilities, quantify threat and vulnerability criticality for being able to prioritize prevention measures.
Threat modeling aims at creating a list of areas or services where you (or your systems) are most vulnerable, the risk of experiencing an attack to these areas, what you can do to mitigate that risk, and to prioritize the order of risk mitigation. What follows from this process, regardless of which specific method is employed, is your threat model.
This more detailed explanation addresses the question surrounding what is threat model in the cybersecurity industry. This has become a necessity in enterprise IT environments.
But threat modeling is also a great practice for those of us who are looking to improve their personal privacy and security online. We will move forward and discuss the in’s and out’s of threat modeling, some of the major methods, and how private persons can learn from these practices and improve their digital security posture.
Industry Standards
In the cybersecurity space, there is lots of talk about the CIA, no not the one with the suits and helicopters, but the CIA Triad. The CIA triad is an acronym made up of the following concepts: Confidentiality, Integrity, and Availability.
Confidentiality for us means that our data should only be available to authorized persons. For the privacy enthusiast, this could mean yourself and friends or family.
Integrity means that your data remains complete and accurate. It is no good if your data is secure, but when you need it there is nothing left but a corrupt file.
Availability means that if the security system we are building or using must be able to provide us with access to the data when we need it.
I can store an encrypted copy of my favorite music on an external drive, lock it in a safe, and bury it in the backyard; sure it is confidential and hopefully there is no data loss, but this is certainly lacking in availability. Balancing these three concepts is crucial when developing your own threat model. Your final model will likely lean towards some of these more than others and that is alright. What is important is that you are working towards a personalized security model instead of taking the one size fits all approach.
When we are choosing what kind of services we wish to use to solve certain problems these three properties must be kept as guiding principles.
A Few of the Big Acronyms in InfoSec
- STRIDE: The STRIDE threat model is an acronym introduced by Microsoft for identifying security threats. It stands for Spoofing, Tampering, Repudiation, Information Disclosure (think data breaches), Denial of Service, and Elevation Privilege. These are threats not only faced by corporate security teams, but everyday internet users.
The never ending wave of spam that email users encounter, those SMS messages pretending to be a child with a new phone number, and bank deposit fraud are all cases of spoofing which are experienced by millions every day.
- OWASP: The Open Worldwide Application Security Project is a community of security experts and researchers who regularly publish articles, tools, and lists ranking the Top Ten security threats. The latest version of the OWASP Top Ten lists includes the often overlooked danger of outdated software and hardware. This threat impacts anyone using a digital device and far too many individuals choose to skip those pesky update notifications. Their top 10 list is worth reviewing as OWASP is highly recognized in cyber threat modeling.
- MITRE ATT&CK: ATT&CK is an open and accessible knowledge base for security professionals and private persons alike. While many of the threats may not apply to the technology you use in your daily life, but MITRE provides an excellent resource for building your security know-how. Particularly important for those of us who are looking to increase our online privacy are the threat groups Reconnaissance and Collection.
Security and Privacy: Two Sides of a Coin
Ok, bear with me for just a few more terms. Security researchers Marit Hansen, Meiko Jensen, and Marin Rost published a paper expanding the CIA triad to focus on introducing better privacy protections to your threat model. They introduce the concepts of Unlinkability, Transparency, and Intervenability.
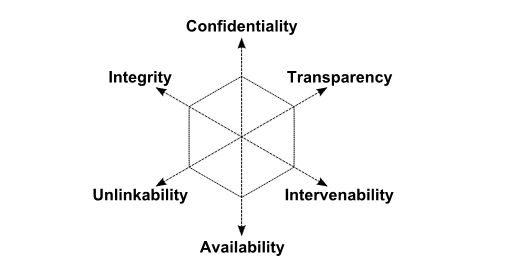
Unlinkability is defined as “the property that privacy-relevant data cannot be linked across domains that are constituted by a common purpose and context.” This means that it should not be possible to link you as a person to your online data.
At Tuta, we have made it easy to create an email account in full anonymity. This allows you to build the epicenter of your digital life without providing any personal data that could be linked to you.
Transparency is “the property that all privacy-relevant data processing… can be understood and reconstructed at any time.” This is focused on the end user’s rights to know what is being done with their data. By publishing our code completely open source, Tuta makes a point of protecting your data and offering full transparency.
Intervenability is a service making “intervention possible concerning all ongoing or planned privacy-relevant data processing.” This refers to giving users control of what happens with their data. This stands against the invasive practices of Big Tech which abuse their access to your data like Google with its search monopoly in pursuit of profits and market control.
Building Your Personal Privacy Threat Model
With all of these long words and acronyms in hand, we can began evaluating our own privacy model. First, let’s think about what kind of technologies you are using. If you are not investing in cryptocurrency, you won’t need to worry about protecting a crypto wallet. Take a moment and review the most important devices in your life to better decide on your threat model.
Your results will vary and you don’t need to finish with anything comparable to a complete OWASP threat model, but certain elements from these industry standards can be helpful to consider.
Now that you have taken a tally of your devices, you can think about what services you are signed up for and where they connect to – and which ones you must never ever lose for one reason or another. Do you have many different online accounts all linked to a single Gmail account? Did you recycle passwords without using two-factor authentication (2FA)? These are things that should pop-up as red flags.
During this process you might find certain services which act as bottlenecks, these are often referred to as single points of failure. If they break, get hacked, or we lose access to them, then our digital life is forfeit. Remember to avoid the creation of single points of failure when reviewing your attack surface.
A common single point of failure is the email account. Lots of people only have a single email account that acts as the root for all their online accounts. This is a prime example because if I create a weak password and don’t use 2FA, I am putting myself in a high amount of risk. Here we can start looking for solutions to mitigate this risk. Choosing to implement password managers to create unique passwords and using a strong form of 2FA like a Yubikey, will strengthen your security posture against attacks toward your email account.
This is a very small example of what threat modeling could look like. Of course, you can go much further and look into many different areas beyond email. This also depends on your lifestyle and personal security needs. The average person won’t have the same security threat model as Edward Snowden. Things to consider when thinking about where your threats may be coming from, it is important to keep in mind things like your occupation, demographics, and your location. Threat models are as unique as you are! Don’t expect your privacy and security requirements to be identical to someone else’s.
If you were an employee of a three-letter agency like the NSA, CIA, or FBI you could become a person of interest to members of competing agencies from other nations so naturally your threat model would look much different to the average Joe’s. This should impact your consideration on what kind of threats are realistic.
The average person is likely ok focusing on avoiding data brokers and hackers exposing their data through data breaches when doing their threat modeling. Some might argue that this threat applies to everyone.
If you are a member of a persecuted group or live in an oppressive country, your security concerns will need to go beyond just using secure passwords as your physical security is also at risk. If you are impacted by legal restrictions on reproductive health care, this should be considered when building your threat model.
Steps To Increase Your Security
Once you have determined what the major threats against your privacy might be, you can begin choosing the solutions to protect yourself and your data.
Step 1: Choose a secure email provider
The first step for protecting your online privacy should be choosing a secure email provider. Nearly all online accounts will ask for an email address, so starting with a strong defense is a must. Tuta offers full end-to-end encryption to protect your data both over the wire and at rest leaving you with a safe starting point for communication, creating calendars, and organizing your contacts.
Step 2: Protect your login
Protecting these accounts requires strong passwords and 2FA. This can be achieved by choosing the best password manager to fit your needs and preferences. We’ve created a list of our favorite password managers to help you decide.
By following these steps, you will have started responding to your personal threat model. The privacy journey is a marathon and not a sprint, but you can pat yourself on the back because if you have created a secure email account and have adopted a password manager to create strong and unique passwords for every account, you will have greatly reduced your risk when data is exposed in a breach. A quick change of password for that specific service and a watchful eye for incoming phishing mails will go a long way.
Step 3: Don't Stop Learning
This is the most important step in privacy, cybersecurity, and threat modeling. Once you’ve taken the first steps you can start widening your scope, do you use a mobile device for sending messages to friends? This is a chance to review the threats to your privacy. WhatsApp may provide end-to-end encryption but if you are concerned with data mining Big Tech companies, you might want to review alternatives. What about your home internet connection? Are you using a VPN? Should you consider using a PO box for receiving packages instead of having them delivered to your home? The list of new and exciting topics in the privacy space doesn't stop growing.
Getting involved in the wider privacy community through articles, forums, podcasts, and books are great ways to continue boosting your privacy knowledge. By working together and sharing our experiences we can all increase our online privacy and security.
Stay safe and happy encrypting!