Time for a Google calendar alternative: Sharing a Google calendar to the public is easy - and dangerous.
Do you know how easy it is to accidentally share a Google calendar? Check out the best alternative for privacy as Google might be leaking your data.
Update 2021-09-28: Check this YouTube video to learn how easy it is to (accidentally) make a Google calendar public.
Feature gone wrong
A recent scandal shows that anyone can make their personal Google calendar public with a few clicks, even unintentionally. If you are using a Google calendar, better check now if your calendar is publicly visible. If it is, you can manage the status of your calendar here in your Google settings.
While this is an intended feature by the Google calendar, it puts everyone's data at risk. Most people using online services are used to sharing private information - calendars, data stored in the cloud, etc. - with others. This is usually done via a shared link, and only the person knowing the link can access the data. This, of course, is not secure, but it is okay for non-sensitive data.
Sharing the Google calendar, however, is a completely different story: Once shared publicly, Google includes the calendar in its search index, which makes it easy for others to find your data. On top of that, anyone can easily find any public calendar by just putting the email address of the person you are looking for in this URL: https://calendar.google.com/calendar/b/1/r?cid=users_mail_address@gmail.com
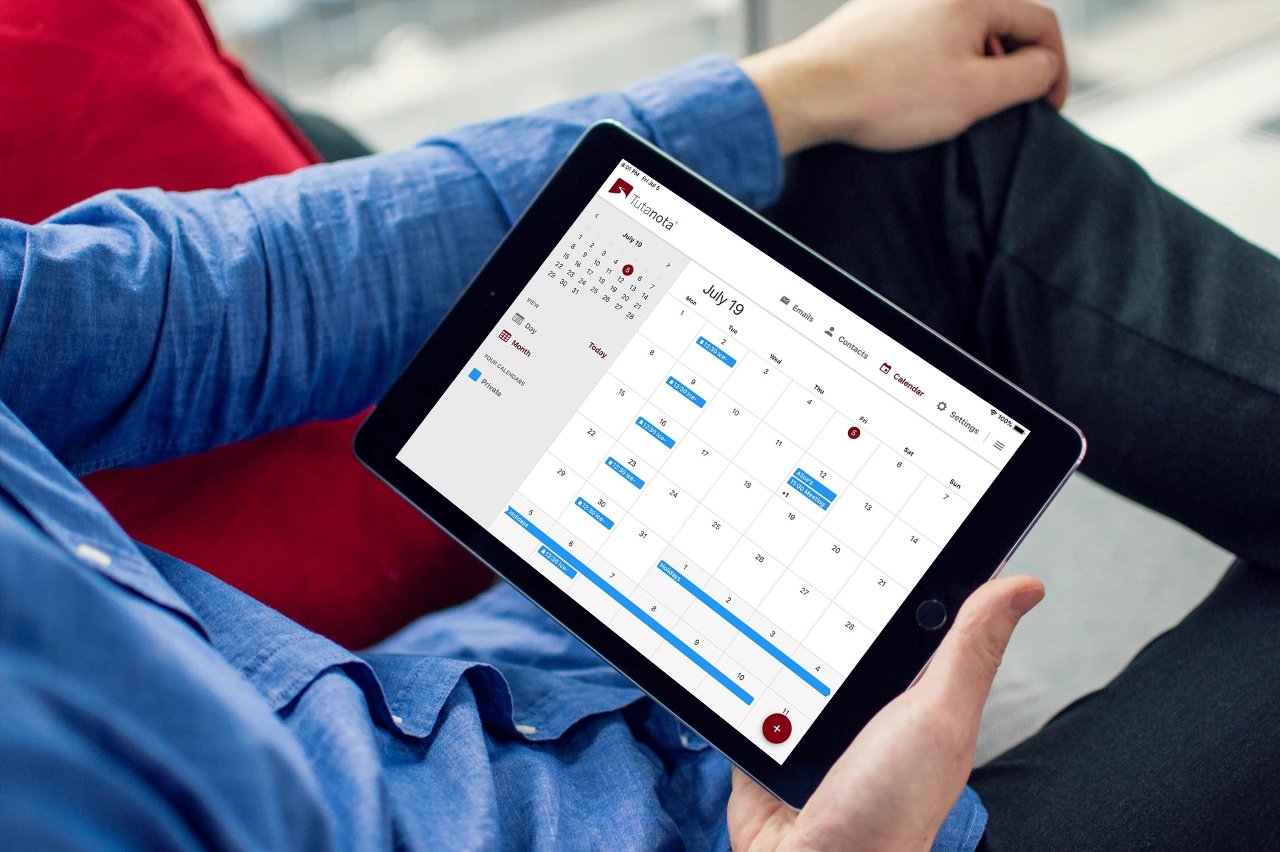
Best Google calendar alternative for privacy: Tutanota calendar.
The encrypted Tutanota calendar is a perfect Google calendar alternative for privacy fans. The data is protected with automatic end-to-end encryption and you can even share the entire calendar privately - not publicly.
Public sharing is a company risk
As the Google calendar is also being used by companies, Google's sharing feature puts sensitive company data at risk. For example, Shopify rewarded Brandon Nguyen $1.000 for disclosing that some employees had set their Google calendar to public, thus, leaking information such as
- New hire information
- Internal presentation
- Zoom meeting links: These meetings can be accessed without login which puts a lot of internal information at risk.
Exploited by malicious actors
Public calendars can be easily searched for and the data contained exploited by malicious actors, for example for sophisticated email phishing attacks.
Some public calendars also let anyone add links to the calendar, which is a settings option in Google. This poses a severe risk as malicious actors can easily add malicious links to a public calendar without anyone noticing.
Is Google Calendar safe?
Using Google Calendar - particularly in a business setting - you have to be aware of the risk: Employees could publicly share calendars and, thus, leak sensitive business information on the world wide web. For that reason, it is not safe to use the Google Calendar in a business environment.
However, it is possible for organization admins to limit or turn off the sharing outside of the organization. As an organization admin, you can check here how to limit the sharing ability of employees.
Time for a Google calendar alternative
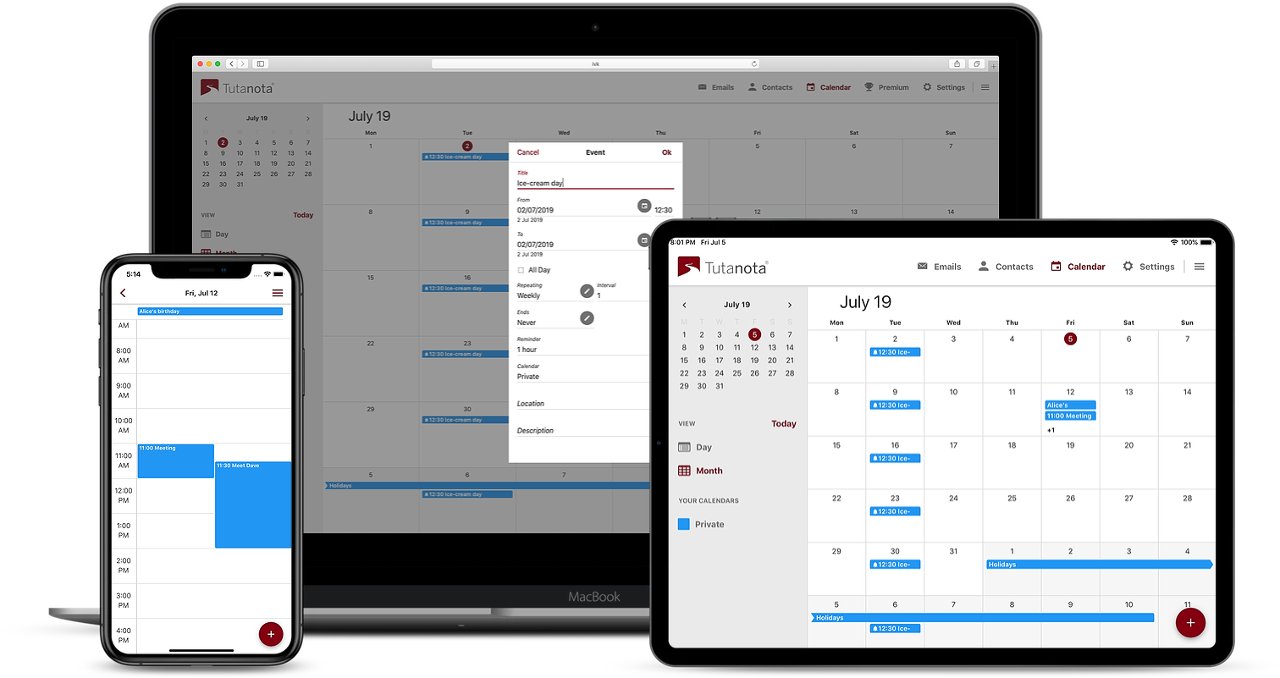
The Shopify scandal shows that it is time for a Google calendar alternative for privacy. When it comes to protecting your private data, the best choice currently available is the Tutanota Calendar. This zero-knowledge calendar is fully encrypted so that no one can spy on your private appointments.
Private sharing
Of course, you can also share the Tutanota Calendar, but only securely encrypted. This means that not only is there no risk of accidentally sharing the calendar publicly, there is also no risk that a link of a shared calendar is passed on by someone you shared the calendar with.
The Tutanota Calendar is always shared encrypted with other Tutanota user. Only the people you share the calendar with have the ability to decrypt the data. This means that no one else, neither we as the provider nor malicious attackers, can access your private data.
Our calendar remains a vital piece of the Tuta experience. Our team is dedicated themselves in recent months to increasing the features and functionality of the encrypted calendar. The latest addition has been the ability to search all your calendar events to find just what you are looking for quickly and easily.
This is what we at Tutanota stand for. We use built-in end-to-end encryption to secure your email and your calendar. We are committed to protecting your data to the maximum so that no one can abuse it.
Check out our comparison of Google Calendar, Microsoft Outlook Calendar and iCloud / Apple Calendar to learn why the Tutanota calendar is a great alternative, particularly when privacy matters to you.