NSO's Pegasus Scandal: Zero-Day, Zero-Clicks, Zero-Privacy?
Why the trade in cyberweapons must be banned just like it's the case with nuclear weapons.

Pegasus: From Myth to Malware
On July 18th, 2021 the scandal on Project Pegasus dragged the mysterious NSO Group back into the public view. Pegasus is a spyware program developed by NSO Group and is a flagship cyberweapon for the surveillance of mobile devices.
This piece of malware was distributed globally and has been used for direct surveillance of - amonth others - "nearly 200 journalists around the world whose phones have been selected as targets by NSO clients" as Forbidden Stories reports. Under the guise of national security, governments across the world have purchased this program in order to put pressure on journalists, activists, and their political opponents.
Despite the present spark in media interest, Pegasus is not a new tool in the international surveillance scene. According to Amnesty International's "Forensic Methodology Report", the spread of Pegasus began as early as 2016 and continues today in 2021.
How Pegasus works
In 2016 human rights activist Ahmed Mansoor received a text message on his iPhone, upon further investigation by Citizen Lab it was discovered that this was a classic spear-phishing scheme seeking to install the Pegasus malware onto his device. "Had he tapped on the link, the phone would have been plundered. Huge amounts of private data: text messages, photos, emails, location data, even what’s being picked up by the device’s microphone and camera."
As of 2019, Pegasus no longer needs a target to tap on that suspicious link to fall victim. NSO has repeatedly exploited zero-day vulnerabilities in messaging platforms such as WhatsApp and more recently iMessage. These zero-day exploits take advantage of security vulnerabilities in programs, operating systems, or mobile applications. The current iteration of Pegasus can infect iOS devices running at version 14.6 or earlier. Once the device has been infected, the program can quickly establish root privileges. The attacker using Pegasus will have complete control over the device.
If you were to become of interest to any of NSO Group's customers, all they needed was your phone number to infect your device. You did not need to click on a link or download a file for Pegasus to be remotely installed on your Android or iOS device. According to Amnesty International "a successful 'zero-click' attack has been observed exploiting multiple zero-days to attack a fully patched iPhone 12 running iOS 14.6 in July 2021." A full list of these exploits can be found in Amnesty International’s Forensic Methodology Report.
Apple released iOS version 14.7 on July 19th and now the world is counting down until the next zero-day exploit is being discovered. In the meantime, a new tool has been released called the Mobile Verification Toolkit which can be used to determine whether or not a device has been compromised by the Pegasus malware. However, this toolkit is complicated to use.
The growth of the cyber-arms industry
In light of these recent disclosures, we are getting a glimpse into the growing cyber-arms industry. The technology acts like a virus: All that it does is it infects smartphones to spy on their owners. If that is not bad enough as such, this virus technology is regularly sold to anyone who can afford it.
You don’t need to scavenge seedy websites to find this software. NSO Group operates like any other government contractor where everyone can see them. A quick search will bring you to "nsogroup.com" where you can contact NSO Group with inquiries regarding prices and potential discounts for weapons of mass surveillance. The main banner on their website is currently advertising "Eclipse: Protect Your Skies" which is a drone platform which can be used to takeover and confiscate "unauthorized commercial drones".
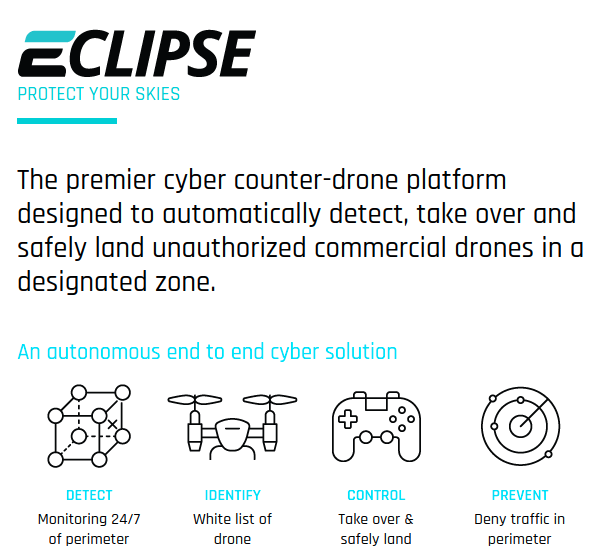
This brazen advertising showcases the growing legitimacy of an industry which once existed on darknet markets or hacking forums.
But what is the difference between an organization like NSO Group who are permitted to work openly with government entities and the hacker group DarkSide who are prosecuted for the distribution of ransomware programs?
It appears that it's only a matter of clientele.
Pegasus poses a threat to privacy
Pegasus and the rise of the surveillance industry pose an immeasurable threat to journalists, political activists, and citizens like you. Security vulnerabilities are not going to go away and there is no such thing as perfect security. This begs the question, what can we as everyday people do to protect our devices, our privacy and our personal data in light of this scandal? What Claudio Guarnieri of Amnesty International's Security Lab - who as a security expert makes use of Secure Connect on his website - told the Guardian was less than optimistic,
"This is a question that gets asked to me pretty much every time we do forensics with somebody: 'What can I do to stop this happening again?'" said Guarnieri. "The real honest answer is nothing."
Germany: Use of Pegasus would be illegal
At least, there are some gems of hope to be found in this affair. When questioned by NDR and WDR on whether or not the German authorities have purchased and used this piece of spy software, German officials responded by stating: "'Pegasus' ist schlichtweg zu mächtig, zu potent. Der Trojaner kann viel mehr, als es die deutsche Gesetzeslage erlaubt." (Pegasus is simply too powerful, too potent. The trojan can do much more than what is allowed under German legislation.)
As a consequence, German authorities declined Pegasus when the NSO Group tried to sell it to them. German laws prohibit extensive surveillance of their own citizens; the protection of privacy is enshrined in the German constitution. Thus, the use of Pegasus would have been unconstitutional.
This attitued taken by the German authorities is admirable, when compared to other global intelligence and law enforcement agencies who have taken a more "spy now-change the laws later approach". The German example showcases that legislation can restrict invasive and unnecessary surveillance practices. If strong privacy legislation can hold these agencies accountable for their actions, then every voting citizen still has a means to fight back against mass surveillance.
Beyond the realm of government, tech giant Amazon "has shut down infrastructure and accounts linked to the Israeli surveillance company NSO Group." Regardless of whether this is simply a PR stunt to avoid criticism or a genuine concern for privacy, this action does show that there is still a concern for the negative public opinion towards mass surveillance.
Cyberweapons must be banned
We need to begin treating these cyber-weapons companies as such. They are manufacturing and distributing tools which are used to intimidate and silence. These weapons are readily available to anyone who can afford the costs. It should be noted that when Philip Zimmerman, the creator of PGP, released his free encryption program which only sought to provide a secure communications platform, he was investigated by the United States Customs Service for potentially violating the Arms Export Control Act.
It is scandalous that support for personal privacy earns a federal investigation, but disregarding it entirely earns a well-funded contract.
In an interview with the Guardian, Edward Snowden hits the nail directly on the head, "There are certain industries, certain sectors, from which there is no protection, and that’s why we try to limit the proliferation of these technologies. We don’t allow a commercial market in nuclear weapons."
While the majority of internet users will not be targeted by this program, there is a chilling effect on those who fear drawing attention to themselves. High profile targets who fear government surveillance would be advised to regularly switch devices and phone numbers to prevent persistent tracking by spy tools like Pegasus.
Snowden closed this interview with a call for solidarity and activism against the growing surveillance industry: "The solution here for ordinary people is to work collectively. This is not a problem that we want to try and solve individually, because it’s you versus a billion dollar company... If you want to protect yourself you have to change the game, and the way we do that is by ending this trade."
As a privacy-first company we call on international legislators and the voting public to support banning the sale of these cyberweapons. Just as there is no market for nuclear weapons, there must not be a market for the sale of software exploits and malware.